To generate an access key and secret access key pair in AWS, you need to have a Guardian scan user set up and configured to use SSH. The following process describes how to create a Guardian scan user in AWS' Identity and Access Management (IAM) service.
-
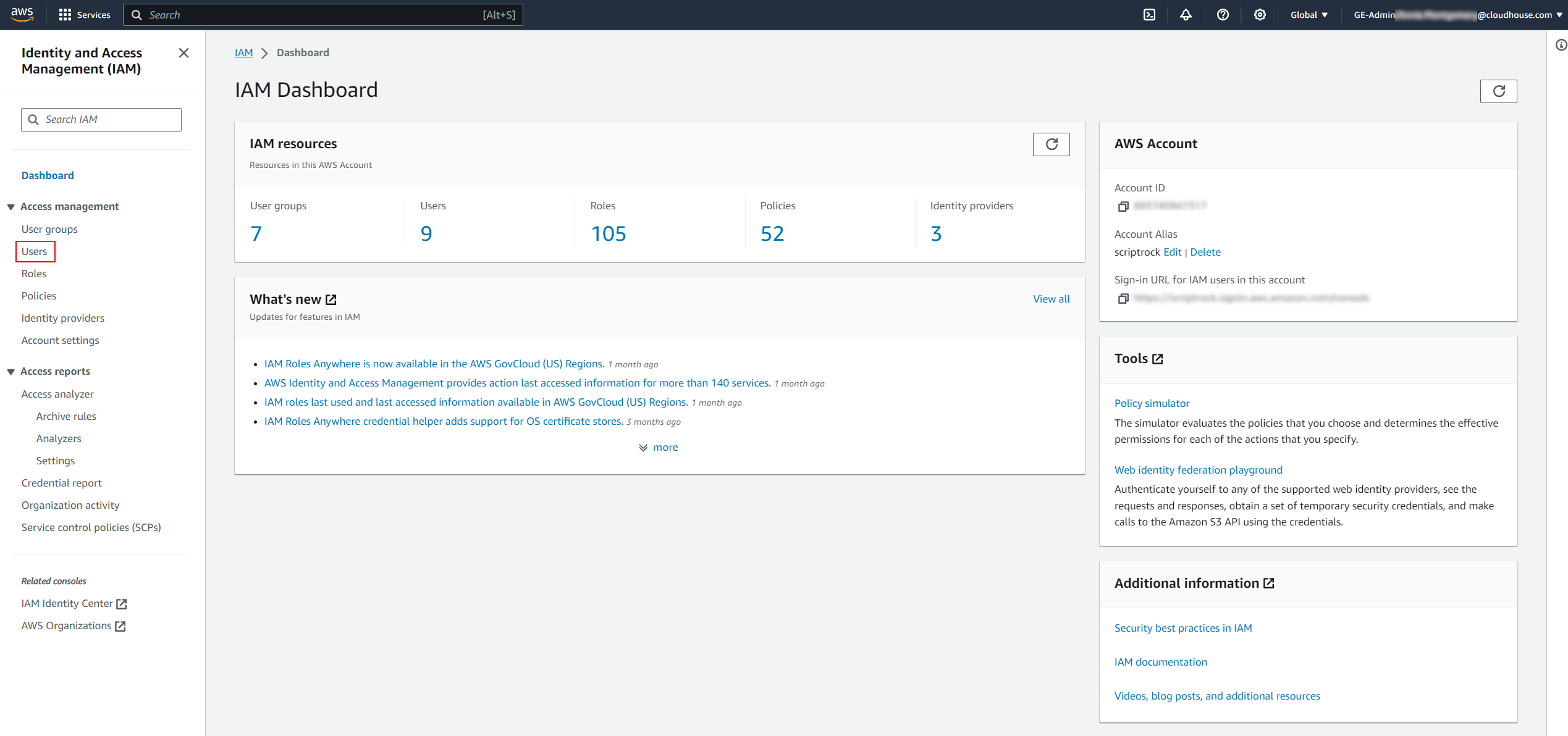
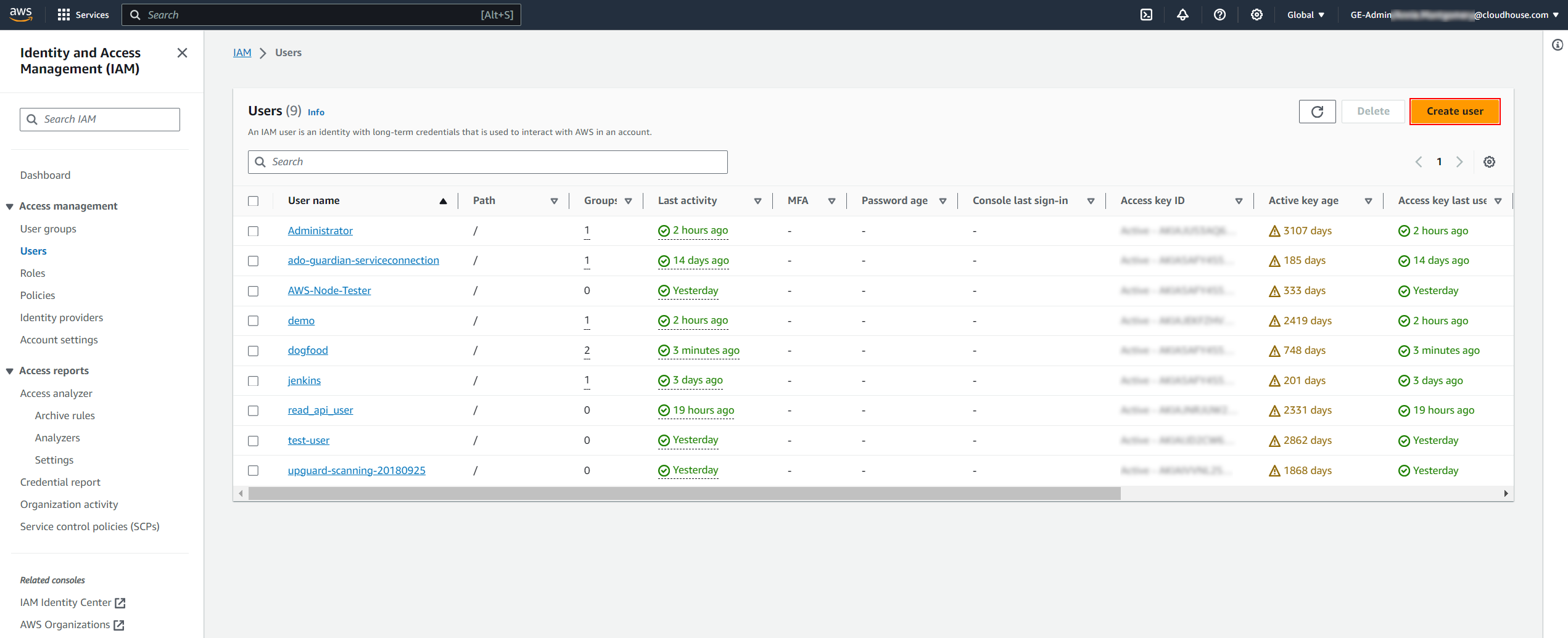
Access the IAM Dashboard (IAM > Dashboard). Then, select Users from the Access management drop-down list on the left hand side of the screen. The Users page is displayed.
-
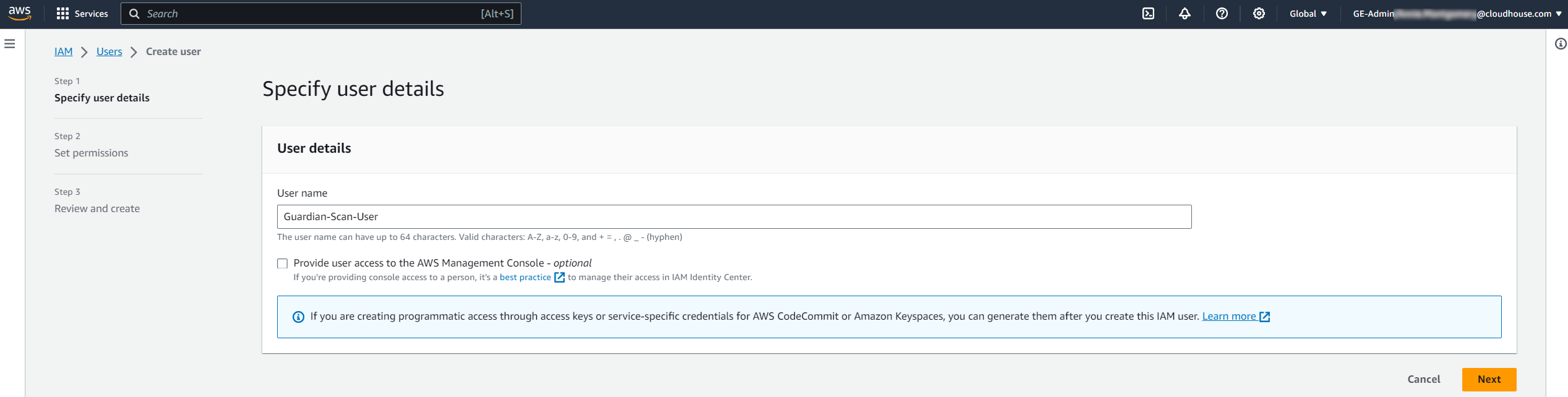
Click to Create user. The Specify user details page of the Create user process is displayed.
-
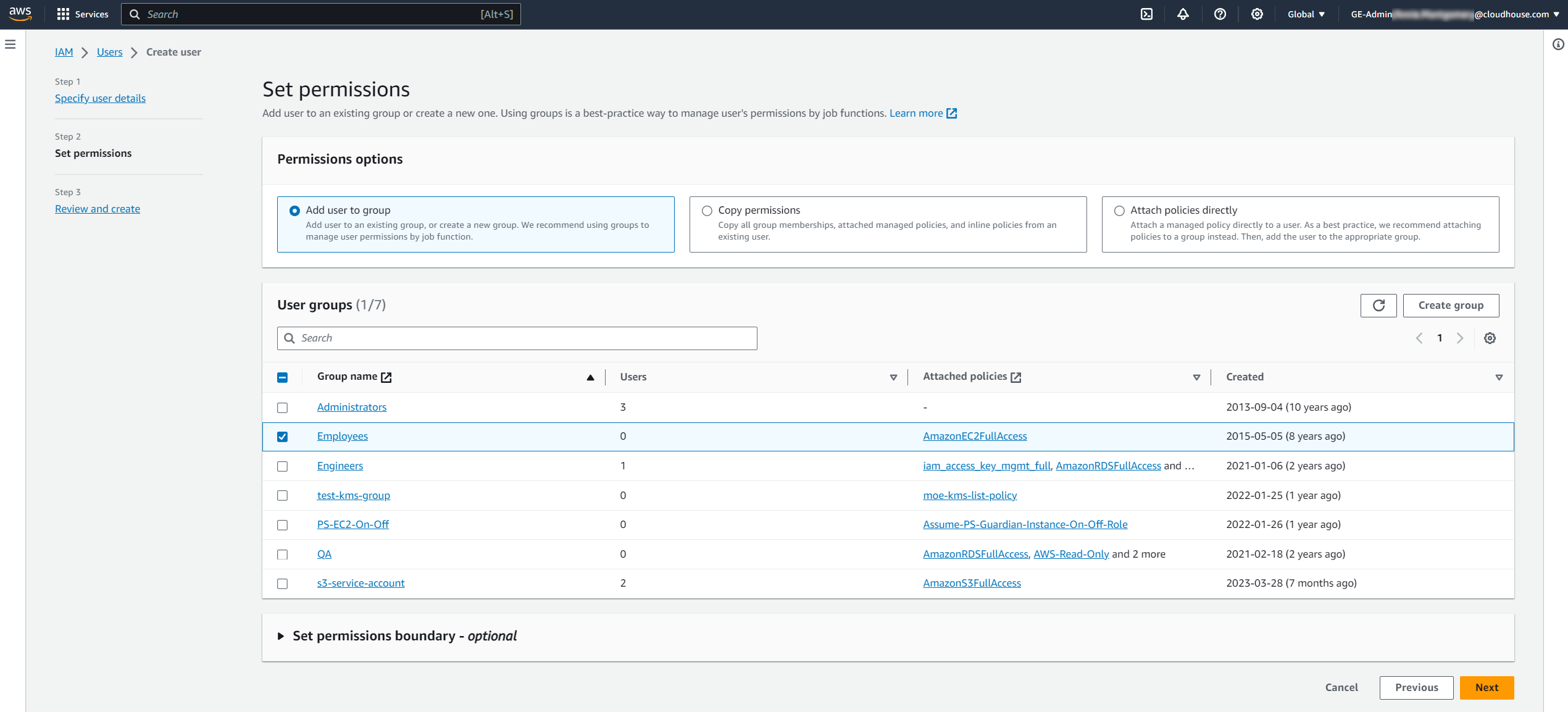
Enter a User name in the field provided, then click Next. The Set permissions page is displayed.
-
Here, we advise adding the user to a group that provides read-only access to AWS. Once complete, click Next. The Review and create page is displayed.
Note: If you need to create a user group with the correct permissions, AWS provide various pre-configured templates for user groups. For EC2 buckets, the 'AmazonEC2ReadOnlyAccess' permissions policy will provide sufficient permissions to allow Guardian access. Full-privilege policies are not required to scan the EC2 instance.
-
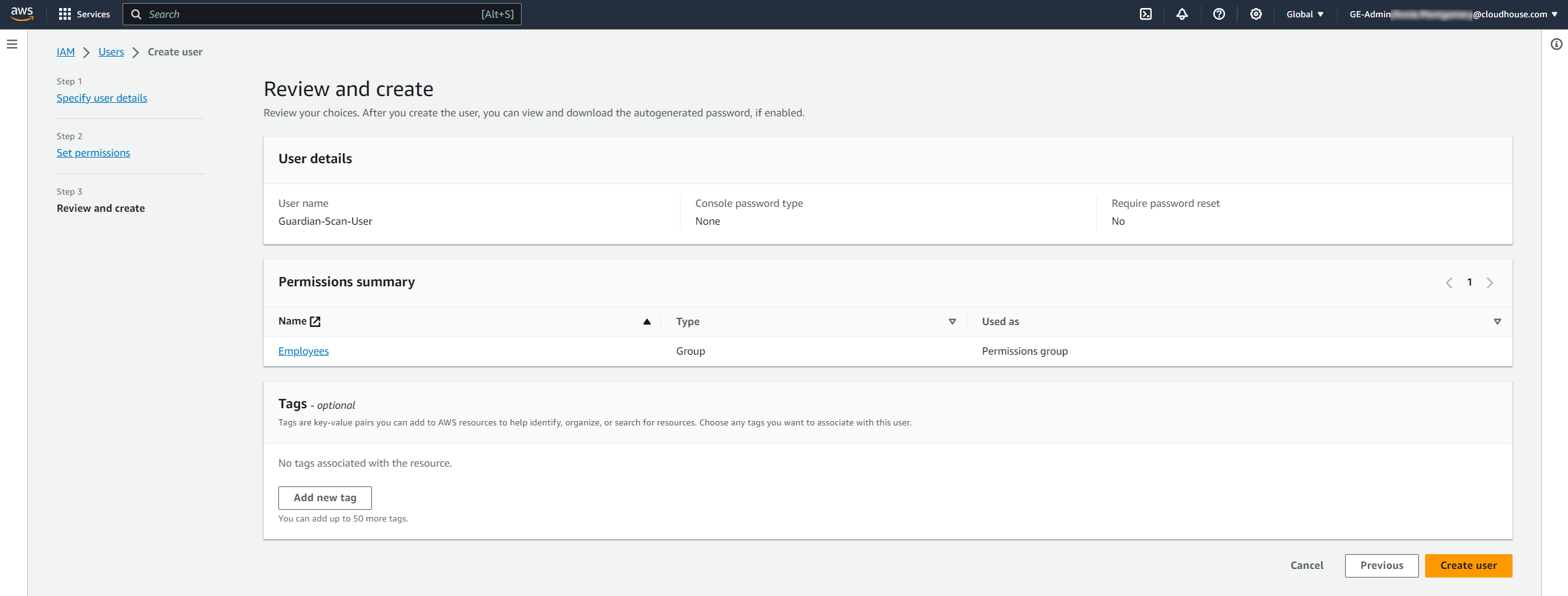
Check the information you have provided is correct; make any adjustments as needed. Then, click to Create user. Once the user has been created, a confirmation message is displayed and it is added to the Users panel.
-
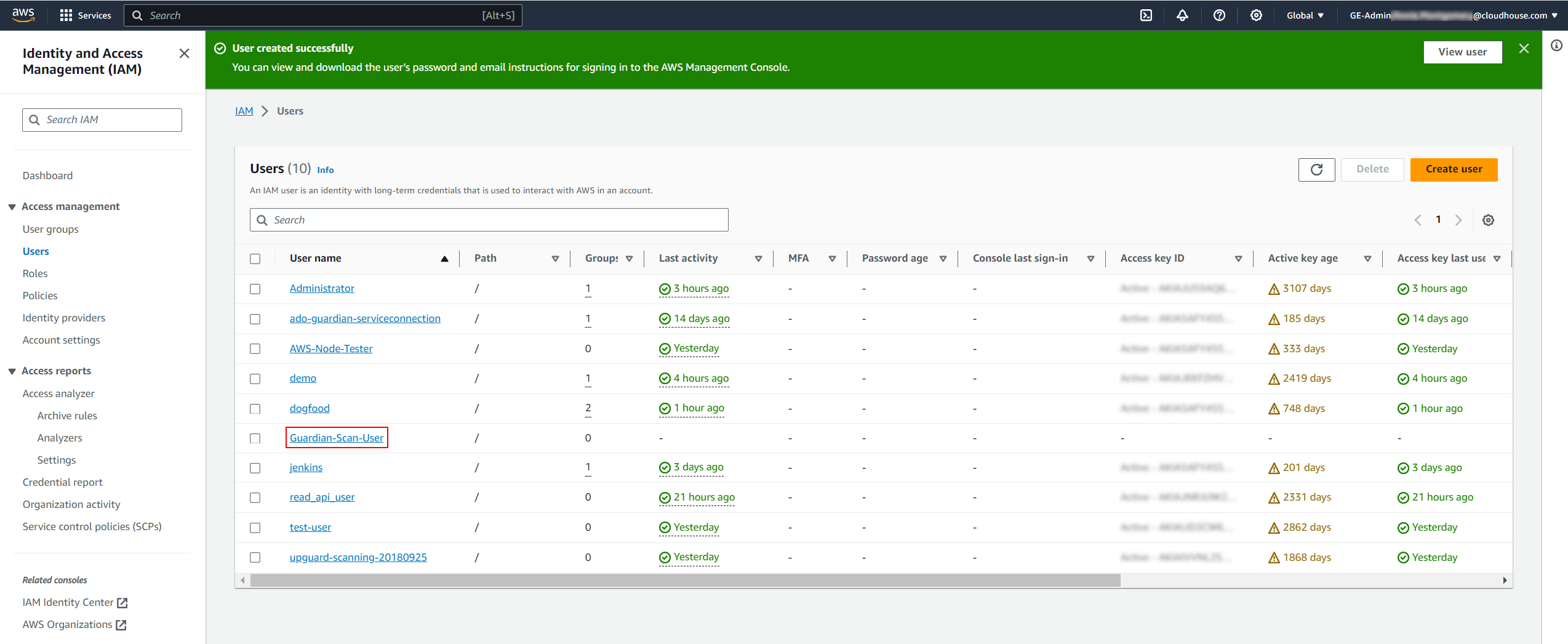
Next, you need to generate an access key and secret access key. Click the User name hyperlink to proceed. The Guardian scan user page is displayed.
-
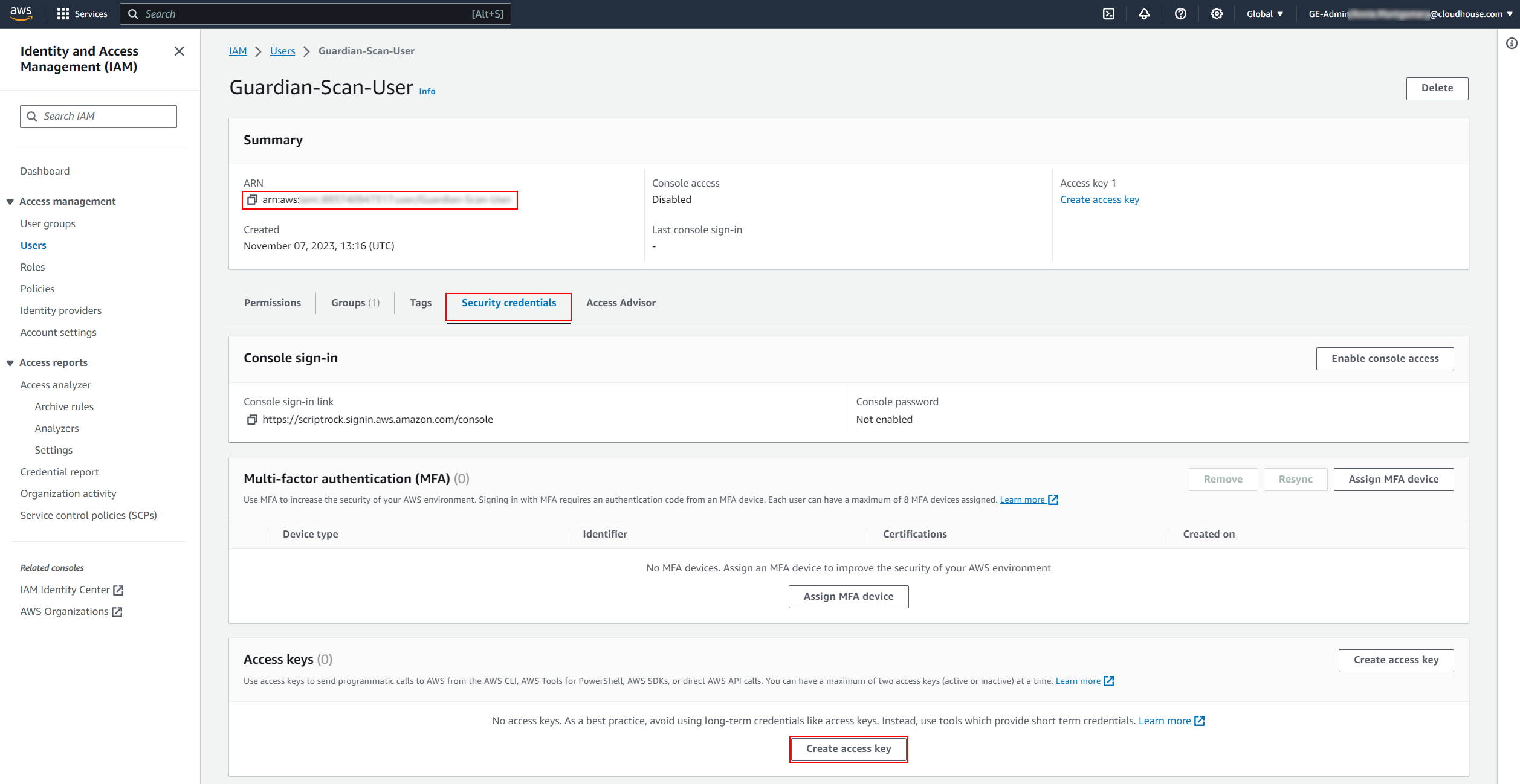
Select the Security credentials tab, then click to Create access key. The Access key best practices & alternatives page of the Create access key process is displayed.
Note: The user's ARN is also displayed in the Summary panel, this value is required for the AWS IAM role ARN field.
-
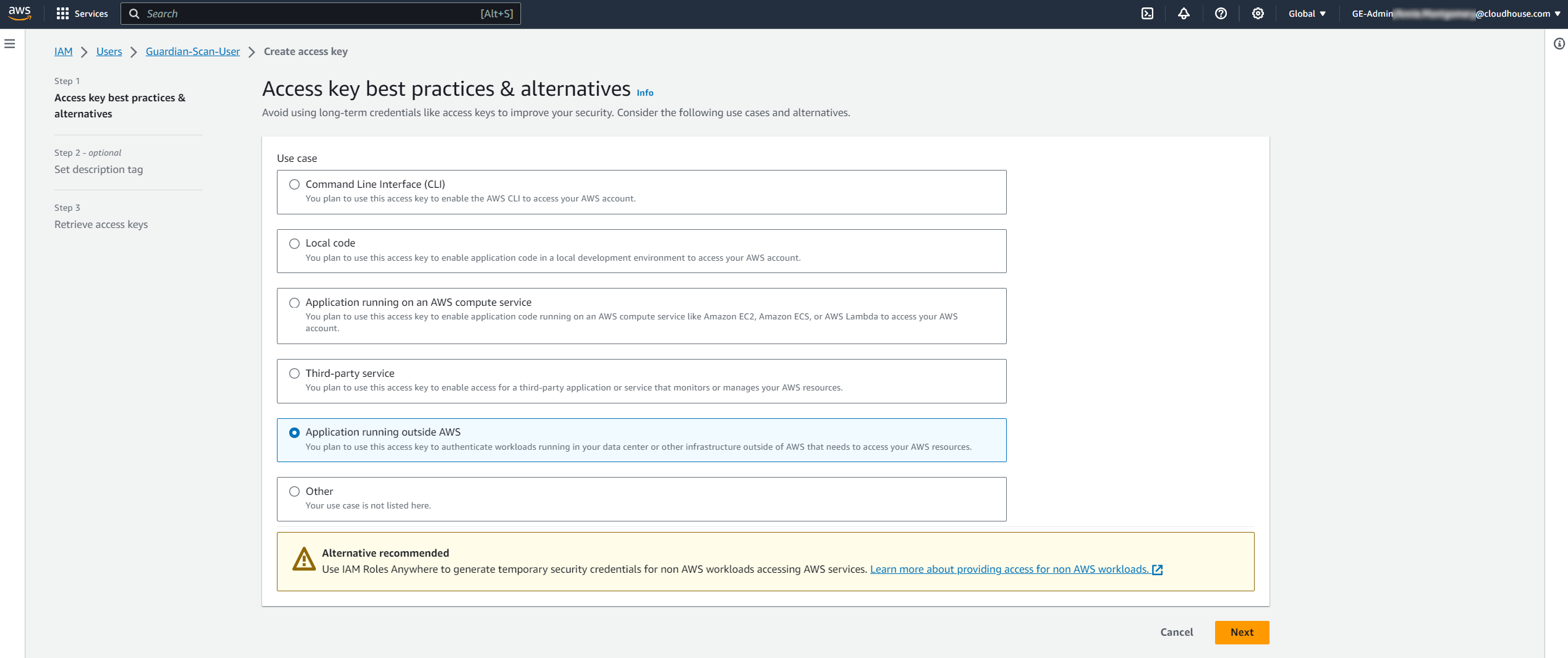
Select the Application running outside AWS radio button, then click Next to proceed. The Set description tag – optional page is displayed.
-
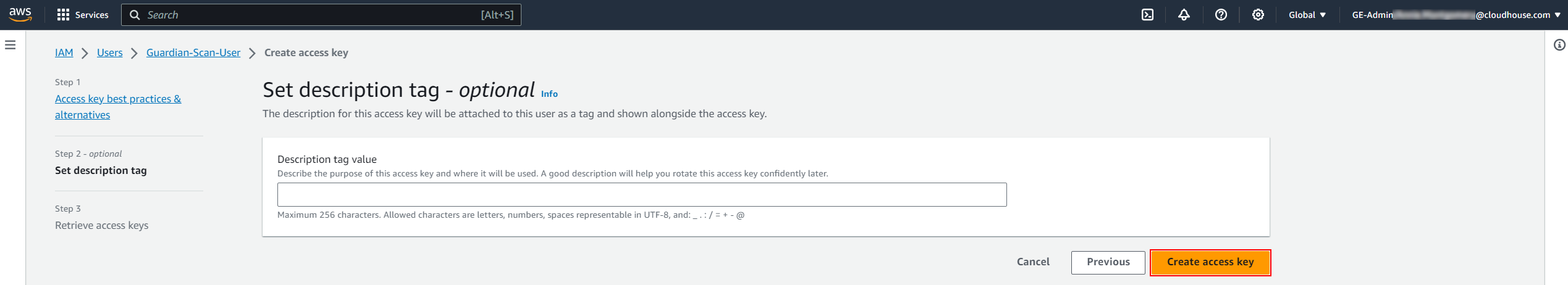
Here, you can optionally set a Description tag value in the field provided. Click Create access key to proceed.
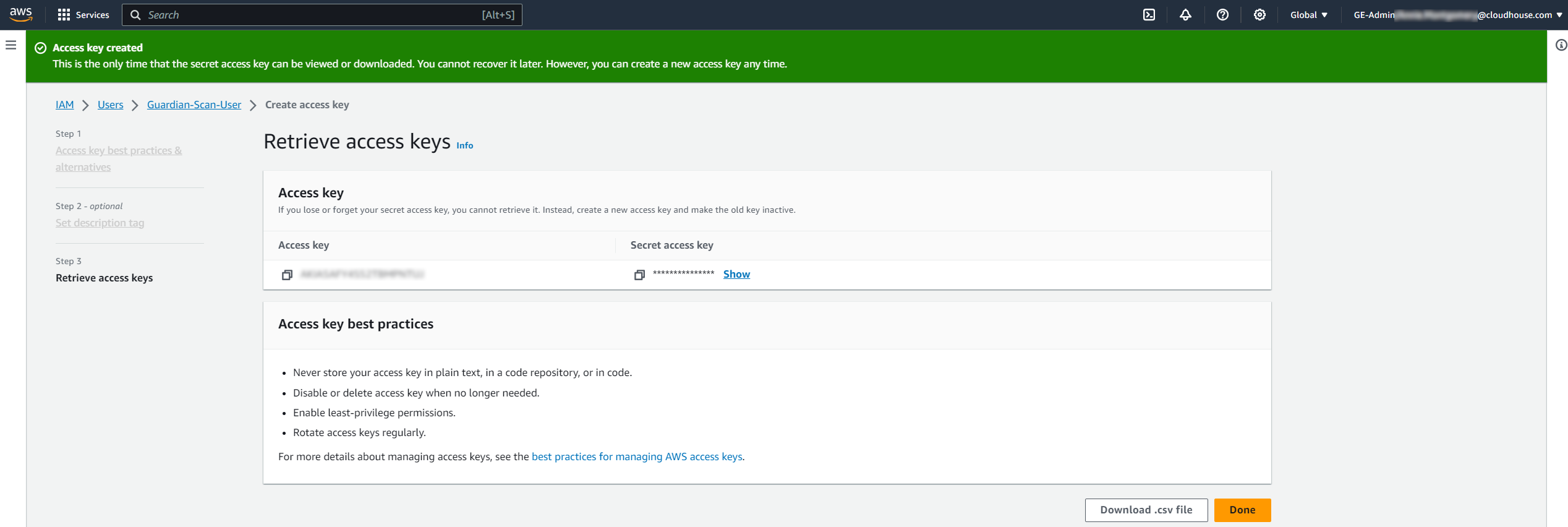
Once the access keys have been created, the Retrieve access keys page is displayed with a confirmation message. Here, you can copy the Access key and Secret access key required for the AWS access key and AWS secret access key fields.
Note: This is the only time that the secret access key can be viewed or downloaded. If you plan to add additional AWS nodes, you may want to download the access keys as a CSV file and store it on your computer for future use. Alternatively, you can deactivate and regenerate the secret access key. However, all existing applications using those credentials will need to be updated.